Poster
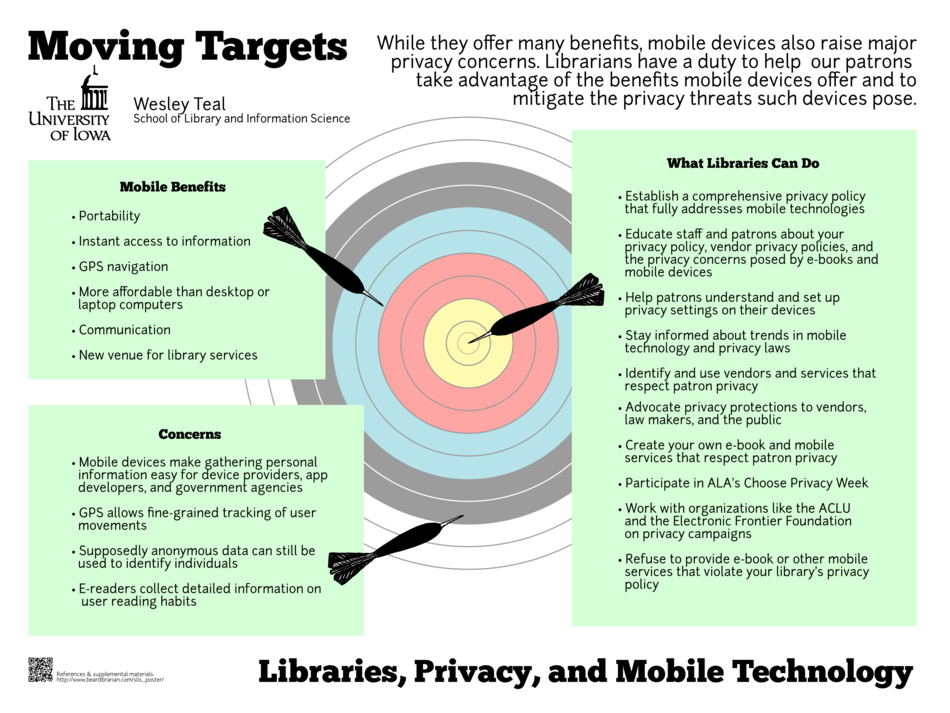
Click on the image above for a full-sized version of the poster. You may also view a transcription of the poster's text.
The proliferation of smartphones, e-readers, and tablet devices, and the rise of e-book vendors like Overdrive present libraries with new ways to serve their patrons but also make it harder to protect patron privacy. Mobile devices allow patrons to access library digital collection instantaneously wherever they are, and tablets and e-readers are convenient and increasingly popular means to read books and periodicals. Unfortunately, mobile devices have made it simple to collect large amounts of users' personal data. Libraries, as traditional guardians of patron privacy, have a duty to educate patrons about privacy concerns, enact privacy policies that deal with emergent technologies, and balance patron desire for e-books and other electronic media with the library's mission to defend patron's right to read (or watch or listen) by protecting their right to do so privately. This poster explores the benefits and drawbacks of mobile devices in regards to library services and offers suggestions of how libraries can protect patron privacy while providing mobile-device-oriented services that more and more patrons desire.

Click on the image above for a full-sized version of the poster. You may also view a transcription of the poster's text.
This poster is accompanied by a brief speech. You can listen to it or read the transcript.
This poster builds on research done in late 2012 which resulted in the paper "A Moving Target: Privacy, Libraries, and Mobile Technology." The paper offers a more in-depth exploration of the issues presented in the poster and outlines the importance of and legal basis for the right to privacy. It is available as a PDF document and as an HTML page.
The target image was created by Alberto Barbati and is used in my poster under the terms of the Creative Commons Attribution-Share Alike 2.5 Generic license.
The dart image is by "johnny_automatic" and is in the public domain.
Alter, A. (2012, July 19). Your E-Book Is Reading You. Wall Street Journal. Retrieved from http://online.wsj.com/article/SB10001424052702304870304577490950051438304.html
Caldwell-Stone, D. (2012, May). E-books and Users' Rights. American Libraries 43(5/6), 60-61.
Chmara, T. (2012, January). Privacy and E-Books. Knowledge Quest 40(3), 62-65.
Cyrus, J. W. W. and Baggett, M. P. (2012). Mobile Technology: Implications for Privacy and Librarianship. Reference Librarian 53(3), 284-296).
Electronic Frontier Foundation (2012). E-Reader Privacy Chart, 2012 Edition. Retrieved from https://www.eff.org/pages/reader-privacy-chart-2012
Gellman, B. and Soltani, A. (2013, December 4). NSA tracking cellphone locations worldwide, Snowden documents show. The Washington Post. Retrieved from http://www.washingtonpost.com/world/national-security/nsa-tracking-cellphone-locations-worldwide-snowden-documents-show/2013/12/04/5492873a-5cf2-11e3-bc56-c6ca94801fac_story.html
Higgins, K. J. (2012, November 1). More Than 25% Of Android Apps Know Too Much About You. Dark Reading. Retrieved from http://www.darkreading.com/risk/more-than-25--of-android-apps-know-too-much-about-you/d/d-id/1138622?
Houghton, S. (2012, August 1). I'm breaking up with eBooks (and you can too) [Web log entry]. Retrieved from http://librarianinblack.net/librarianinblack/2012/08/ebookssuckitude.html
LaRue, J. (2012, January 17). Dear Publishing Partner [Web log entry]. Retrieved from http://jaslarue.blogspot.com/2012/01/dear-publishing-partner.html
McGrane, K. (2012, November 5). Uncle Sam Wants You (To Optimize Your Content For Mobile). A List Apart Retrieved from http://alistapart.com/article/uncle-sam-wants-you-to-optimize-your-content-for-mobile
Sankin, R. (2013, November 22). Mobile-only Internet users face a harsh new digital divide. The Daily Dot. Retrieved from http://www.dailydot.com/lifestyle/digital-divide-mobile-internet-challenges/
Symantec. (2014, January 23). Norton Mobile Insight Disovers Facebook Privacy Leak [Web log entry]. Retrieved from http://www.symantec.com/connect/blogs/norton-mobile-insight-discovers-facebook-privacy-leak
Whittakker, Z. (2014, January 27). Meet the 'Spy Smurfs': Here's how the NSA, GCHQ target iPhones, Android devices. ZDNet. Retrieved from http://www.zdnet.com/u-k-u-s-spy-agencies-scoop-leaky-app-data-new-snowden-leaks-say-7000025628/
Wicker, S. B. (2012, August). The Loss of Location Privacy in the Cellular Age. Communications of the ACM, 55(8), 60-68. doi:10.1145/2240236.2240255